Insider Threats: A Growing Challenge Across All Sectors
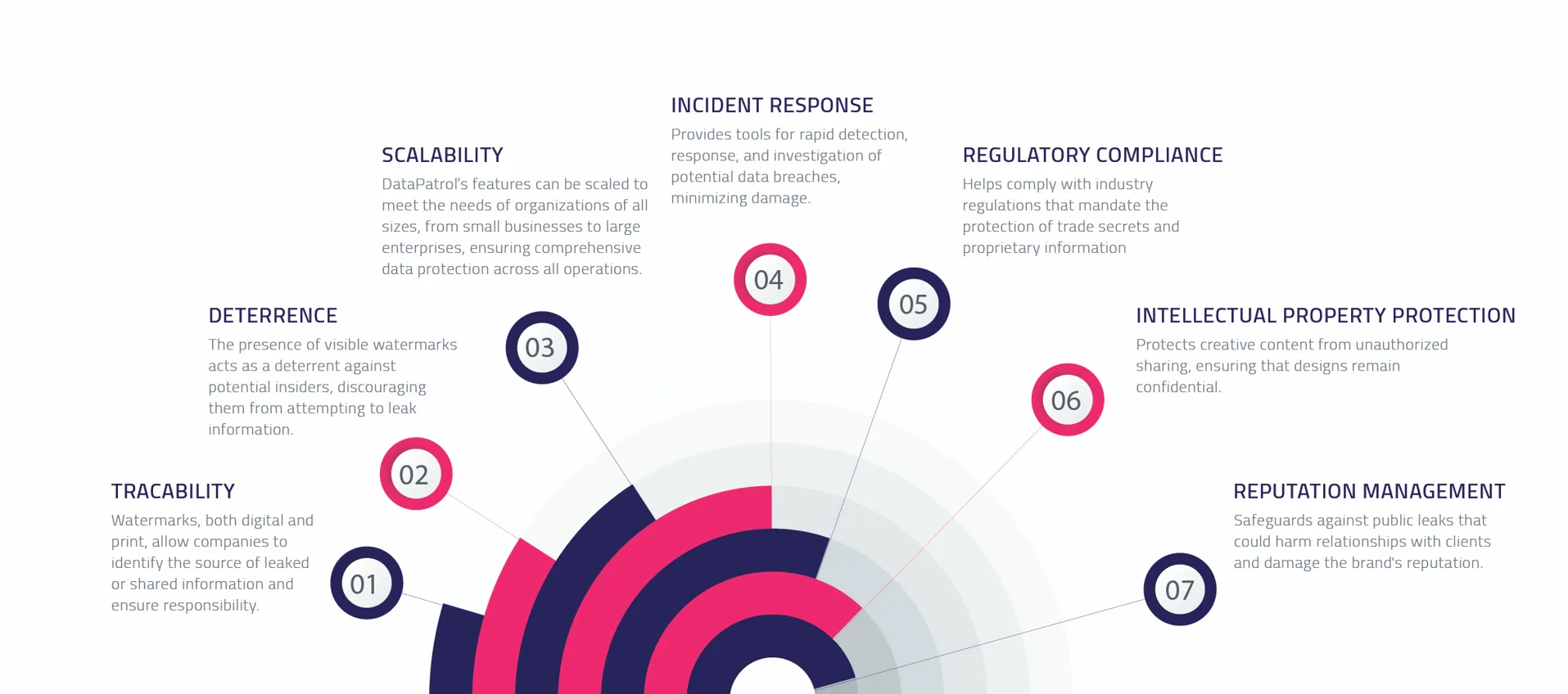
Government, healthcare, financial services, and manufacturing organizations must address the growing challenge of securing sensitive information against internal threats. These threats can cause leaks that undermine trust, finances, and competitive advantage.
KEY INDUSTRY PAIN POINTS

Government
The responsibility of protecting highly sensitive data, such as biometric information, medical records, personally identifiable information (PII), and unique identifiers like Social Security numbers or passports, has been handed to governments.
Protecting this data from internal threats, such as employees who might intend to access and exfiltrate it for their own personal advantage or under outside influence, is the major challenge.
Consider a scenario in which a government employee with access to this confidential data attempts to export it to an outside entity, potentially with the intention of selling it or utilizing it for identity theft.
Protecting this data from internal threats, such as employees who might intend to access and exfiltrate it for their own personal advantage or under outside influence, is the major challenge.
Consider a scenario in which a government employee with access to this confidential data attempts to export it to an outside entity, potentially with the intention of selling it or utilizing it for identity theft.
Financial Services
Employees may try to steal confidential financial information from any system, including client records, transaction information, or internal communications, making the financial services industry particularly susceptible to internal attacks. Such threats might appear in several ways, such as by utilizing mobile devices or screen capture tools to capture screen content.
For example, an employee may obtain access to a client's personal and financial information and seek to export and sell it. In this strictly regulated industry, financial institutions are obligated not just for managing their clients' funds but also for protecting their sensitive information.
Any insider threat can have serious effects, including significant financial losses, regulatory fines, data breaches, a profound loss of consumer trust, and damage to a reputation
For example, an employee may obtain access to a client's personal and financial information and seek to export and sell it. In this strictly regulated industry, financial institutions are obligated not just for managing their clients' funds but also for protecting their sensitive information.
Any insider threat can have serious effects, including significant financial losses, regulatory fines, data breaches, a profound loss of consumer trust, and damage to a reputation
Creative Industry
The creative industry can be extremely vulnerable to internal threats, in which workers or contractors may leak or misuse sensitive intellectual property (IP), such as unpublished content, designs, scripts, or advertising strategies. These leaks can occur as a result of in violation copying, screen captures, or printing of confidential documents, causing significant damage to a company's competitiveness and brand reputation.
For example, a dissatisfied designer working on a video game may attempt to leak early design concepts to a competitors by snapping screenshots, recording a video with his phone, or printing the designs
Such breaches not only compromise the product itself, but they may also disrupt promotional activities, compel premature product releases, and allow competitors to lower the original product's market effect, resulting in financial losses and a tarnished brand image.
For example, a dissatisfied designer working on a video game may attempt to leak early design concepts to a competitors by snapping screenshots, recording a video with his phone, or printing the designs
Such breaches not only compromise the product itself, but they may also disrupt promotional activities, compel premature product releases, and allow competitors to lower the original product's market effect, resulting in financial losses and a tarnished brand image.
Manufacturing
Manufacturing businesses are regularly targeted for their trade secrets, which include product designs, manufacturing processes, and unique technology. Internal threats such as workers selling designs to competitors or using them for personal benefit pose substantial concerns. For example, a production engineer may have access to secret CAD drawings and blueprints for a new product line. They might try to print these designs and share them with a competitor in return for financial gain, thereby damaging the company's competitive advantage and causing considerable financial and repetitional damage.
Healthcare
Healthcare practitioners are responsible for protecting highly sensitive patient data, such as medical records, treatment history, and insurance information. This info is essential. However, internal risks such as staff members attempting to access and misuse this data pose serious concerns.
For example, a hospital employee might take advantage of their access to a high-profile patient's medical records, seeking to leak private information to the media in exchange for money. Such an insider attack might result in significant legal implications for the healthcare provider, including fines and lawsuits, as well as financial losses and irreversible damage to the institution's reputation and trust among patients.
For example, a hospital employee might take advantage of their access to a high-profile patient's medical records, seeking to leak private information to the media in exchange for money. Such an insider attack might result in significant legal implications for the healthcare provider, including fines and lawsuits, as well as financial losses and irreversible damage to the institution's reputation and trust among patients.
90 %
Data Protection
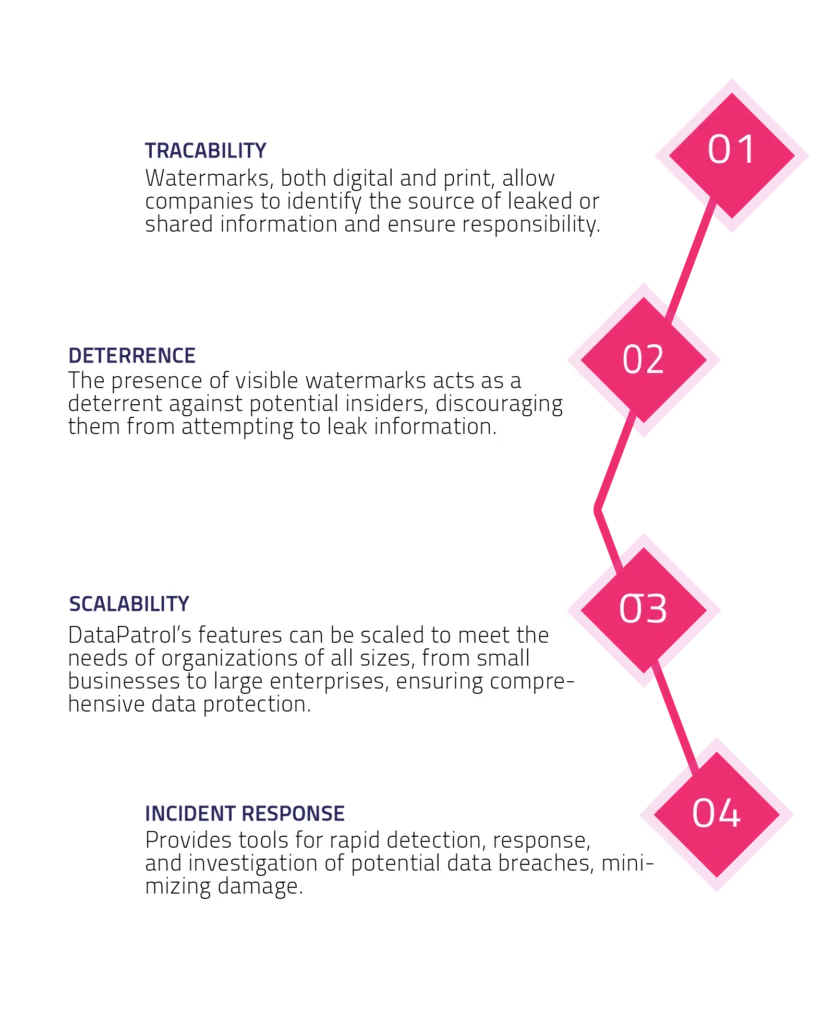
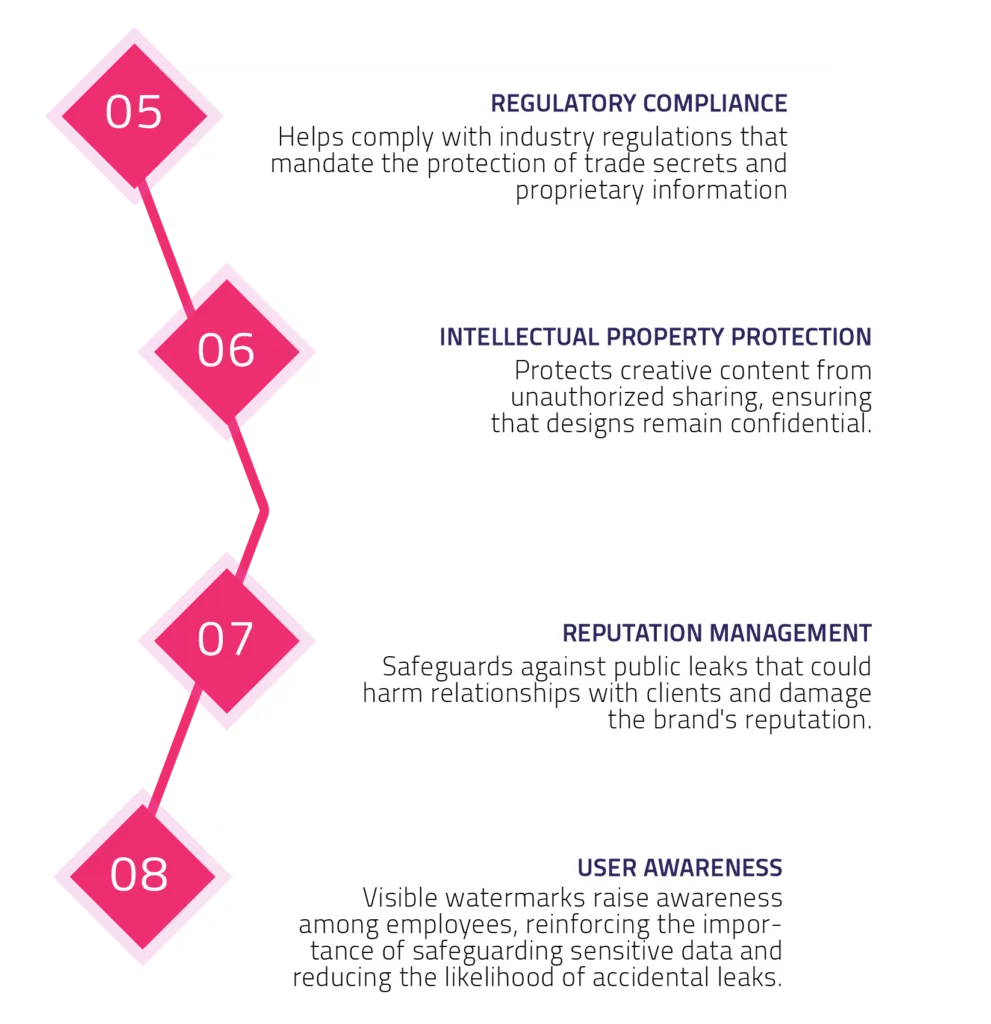
DATAPATROL’S SOLUTION STRATEGY
Some of the methods an insider can use to leak confidential data includes taking photos or screen captures of sensitive information, printing valuable company data, and unauthorized copying of digital data. Since critical data nowadays can be found anywhere, weather in specific in-house applications, online systems, web pages, systems etc. it needs to be protected leakages.
To tackle these critical challenges and protect sensitive information across various sectors, DataPatrol offers a robust set of security features specifically designed to prevent internal threats and ensure comprehensive data security.
This feature places a dynamic watermark on all digital screens —whether on desktops, laptops, or workstations—at the operating system level, embedding metadata like the username, hostname, IP address, system date and system time. Whether in government, healthcare, financial services, manufacturing, or the creative industry, this customizable watermark acts as a powerful deterrent against unauthorized screen captures. It ensures that any attempt to capture or leak information through cameras can be traced back to the responsible party.
DataPatrol automatically embeds a watermark containing user-specific information on any document that is printed. This feature is essential across all sectors, from government to healthcare and financial services, where sensitive printed materials like biometric data, patient records, or financial statements need to be securely managed. If these documents are leaked, the watermark allows organizations to trace the source of the breach and take appropriate action.
This feature prevents users from copying sensitive text data from any digital documents. In industries like healthcare and government, AntiCopy ensures that employees are fully aware and sure about the confidential information—whether it's patient data, or biometric data they insert.
DataPatrol blocks the use of the Print Screen function and other screen capture tools, stopping users from capturing and saving images of sensitive data displayed on their screens. This feature is vital across all sectors, ensuring that critical information, from patient health records to intellectual property and strategic plans, cannot be captured and shared without authorization.
DataPatrol’s WebMark applies customizable watermarks to sensitive data viewed through web browsers, embedding details such as usernames, timestamps, and organizational identifiers. This feature ensures accountability and deters unauthorized sharing or screenshots of critical content. WebMark is especially effective in sectors like law, for protecting legal case files and sensitive client information; finance, for securing banking portals; healthcare, for safeguarding patient data in electronic medical systems; and education, for ensuring confidentiality in online examination platforms. It also supports Private CRMs, Enterprise Resource Planning (ERP) systems, and Custom SaaS platforms, offering robust protection for sensitive information on websites and portals across diverse industries.
DataPatrol’s MobileMark applies watermarks to content viewed on mobile devices, ensuring accountability and data protection without interfering with the device's regular apps or operations. Admins can choose to apply the watermark to content across all apps on the mobile device or specify applications where the watermark should be enabled. For example, a sales representative accessing CRM tools or customer data on their mobile will have a unique watermark with their name and timestamp. Similarly, customer support teams using mobile devices to handle sensitive customer inquiries can have personalized watermarks applied to any information they view.
DataPatrol allows administrators to create and enforce customizable security policies tailored to the specific needs and regulatory requirements, enhancing compliance and security posture.
DataPatrol offers comprehensive monitoring and logging features that capture all significant user activities, system events, and policy changes. Administrators can access system logs, policy logs, machine logs, and audit logs directly through the Admin Panel. This allows for monitoring and tracking user behaviour, ensuring compliance and aiding in audits. These logs provide transparency and enable quick responses to potential security incidents, enhancing overall data protection.
VALUE ADDED