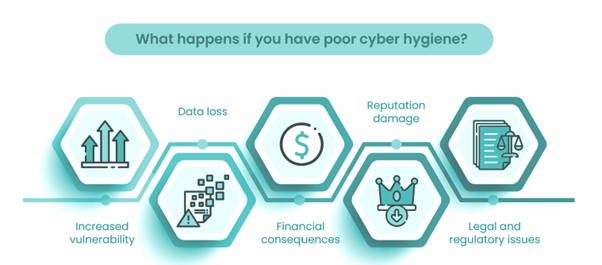
Staying updated with the latest insights and statistics on insider threats is crucial for organizations to mitigate potential risks. Going through the latest statistics, helps you can gain a better understanding of the most recent trends, risks, and strategies that you can use to enhance your organization’s cybersecurity. In this article, we will explore information regarding the various types of insider threats, their costs, and the measures you can take to prevent and prepare for insider attacks.