
Insider Threats Response: Developing an Effective Incident Response Plan
Resources
Insider threats pose a high risk to the security and integrity of organizations. Unlike external threats, insider threats originate from within an organization and potentially exploit their access and knowledge to compromise sensitive data, systems, or operations. To mitigate these risks, organizations are required to have a robust incident response plan specifically tailored to address these internal threats.
Understanding Insider Threats
Not every insider risk becomes an insider threat; however, every insider threat started as an insider risk.”
– Gartner –
Insider threats can manifest in various forms, ranging from accidental breaches due to negligence or ignorance to intentional malicious activities conducted by employees, contractors, or partners. These threats can target sensitive data, intellectual property, or critical infrastructure, causing substantial financial, reputational, and operational damage.
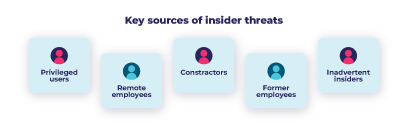
Insider threats are certainly becoming an expensive risk for organizations’ data security, and more difficult to detect. Thus, developing a comprehensive insider risk management strategy is essential to overcome those risks. Establishing an effective insider threat incident response plan is one of the most crucial elements to successful insider risk management.
Key Components of an Effective Insider Threats Incident Response Plan
The time to contain an insider incident has increased to an average of 86 days.
– Ponemon Institute –
Identification and Detection: The ability to identify and detect potential risks is the first step to mitigate insider threats. This involves implementing monitoring systems and protocols that track user behavior, network activities, and data access patterns. Detecting suspicious behaviors should trigger immediate alerts for investigation.
Risk Assessment: Once a potential insider threat is detected, conducting a comprehensive risk assessment is crucial to fast containment. This assessment should evaluate the severity of the threat, the potential impact on the organization, and the involved assets or data.
Response Strategy: A well-defined response strategy should outline clear steps to contain the threat, minimize damage, and restore normal operations. This might involve isolating affected systems, revoking access rights, and implementing temporary measures to mitigate the ongoing risks.
Communication Plan: Transparent and effective communication is vital during an insider threat incident. Stakeholders, including employees, customers, partners, and regulatory bodies, need to be informed promptly and accurately about the situation, steps taken, and the potential impact.
Collaboration and Coordination: Collaboration among various departments—IT, security, legal, HR—is essential to effectively respond to insider threats. Coordination ensures that each team understands its role and responsibilities in mitigating the incident.
Continuous Improvement and Learning: Post-incident analysis and evaluation are important to understand what went wrong, identify security gaps, and use these insights to improve future response plans.
Developing and implementing an effective incident response plan to tackle insider threats is essential in today’s cybersecurity landscape. By combining proactive measures with a well-structured response strategy, organizations can significantly mitigate the risks posed by insider threats, safeguard their critical assets, and maintain customer trust. Constant vigilance, regular training, and continuous improvement are key to staying ahead of these evolving security challenges.
Want to learn how DataPatrol can help you prevent insider threats?
Explore our Solutions
DataPatrol provides organizations with out-of-the-box and user-friendly solutions to secure sensitive and confidential data from unauthorized disclosure.
Request a demo today!








