
Step by Step: Understanding Data Loss Channels and Why You Need Screen Watermarks
In a world where work is increasingly digital, remote, and interconnected, sensitive information constantly moves across multiple channels and access points, from emails and cloud platforms to messaging apps and USB devices. However, while organizations focus on securing data in transit or storage, one silent risk often slips under the radar: the screen, where information is seen, shared, and sometimes… leaked.
Understanding Data Loss Channels
Data loss does not only happen through external cyberattacks. It can be internal, accidental, or simply due to overlooked weak spots in your data security protocol.
So, what exactly are data loss channels?
Data loss channels are the pathways through which sensitive, confidential, or protected information can leave an organization accidentally, maliciously, or through negligence. They represent all the potential exit points where data can be exposed, copied, transferred, or stolen, often without detection. Most security teams are already familiar with these types of channels:
- 📤 Emails: Sensitive attachments sent without encryption or to the wrong contact
- ☁️ Cloud platforms: Easy to access, easier to misconfigure or overshare
- 💬 Messaging apps: Informal chats that often bypass corporate controls
- 🌐 Web pages: Downloaded content, exposed forms, auto-filled data
- 🔌 USB & Plug-and-Play devices: Fast, offline, and hard to track once data is copied
These channels are often monitored and controlled through DLP systems, access controls, or usage policies. But here’s the question: What about data displayed on screens?
Filling the gaps in Data Protection
“If data is visible, it is vulnerable.”
In modern work environments, data is constantly being viewed, not just stored or sent. It is displayed on desktop monitors, shared during virtual meetings, accessed through mobile devices, and visible across multiple platforms, making screens one of the most common and most critical blind spots in data protection.
And what is stopping someone from capturing sensitive data with a screenshot or a mobile camera?
Why Do You Need Screen Watermarks
Adding a watermark to your screens has proven to be the simplest and smartest way to protect sensitive data in real time. A dynamic watermark displays visible identifiers, such as the company logo, username, email address, timestamp, device information and other metadata, making it easy to trace any unauthorized screenshots or photos back to the source.
Screen Watermarks act as a deterrent, reminding users that what they see is being monitored and that any leakage is fully traceable. When collaborating with external partners or clients, screen watermarking also helps you safeguard your intellectual property and confidential information, especially when data is accessed across different platforms, browsers, or virtual environments. And most importantly, a good watermark strikes the right balance: It should be clear enough to discourage leaks but subtle enough to keep the screen readable and usable. After all, security should support your business, not block it.
DataPatrol’s Multi-layered approach to screen security
DataPatrol offers a complete, multi-layered suite of screen data protection tools to prevent insider threats, unauthorized sharing, and screen-based data leaks across all environments. As a next-generation information and data security platform, DataPatrol is built to identify and close the critical gaps in your security protocol, empowering organizations to maintain control, accountability, and compliance without compromising usability.
Here is how each feature supports a complete screen protection strategy:
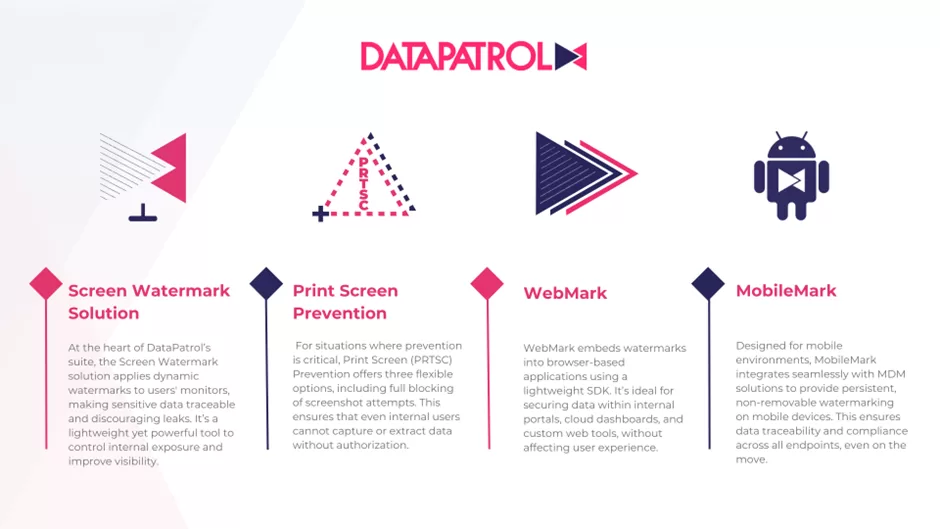
Learn More about our solutions.
Every day, sensitive data is viewed, discussed, shared, and decided upon, all through screens. And yet, screens remain one of the most unprotected data loss channels in enterprise security. Without screen-level protection, even a simple screenshot or shared data can result in unauthorized disclosure. Addressing this blind spot is essential for any modern data security strategy aiming to close all gaps in protection.








