
Insider Threats in 2025: Simple Facts, Big Consequences
Insider incidents are rising in cost and complexity, and they definitely don’t look like traditional attacks. While external threats still dominate headlines, many of the most expensive cases start with someone who already has access: an employee, contractor, or partner. The hard part is: It’s hard to spot risky behavior that looks normal and to act fast.
What’s really driving insider risk
What turns routine into risk is the mix of how people access data, where that data is viewed, and how long issues go unnoticed. Here’s what consistently drives the problem:
1- Routine actions are risky
Most insider incidents begin with everyday actions: logging in, downloading, taking a screenshot, or sharing. By the time it’s flagged, the trail is long and the impact is wider than expected.
2- Security gaps
Data now lives across SaaS apps, cloud stores, internal portals, mobile devices, and remote desktops. Many teams can trace access, but not what actually happened when access is granted and data is displayed.
3- Time multiplies cost
Containment windows matter. Short investigations and decisive controls reduce legal, brand, and recovery costs. Long-running scenarios are expensive.
The human patterns behind the numbers
Behind these statistics are everyday behaviors that don’t look dangerous until they do. Insider risk isn’t a single threat type. It’s a wide range of intent and mistakes that hides inside normal daily work. These patterns help focus attention on where risk most often begins.

- Negligence is common.
Human error is the major cause of insider negligence. Mis-delivered files, weak sharing settings, and unapproved exports happen more than malicious acts and add up across the year. - Compromised credentials drive the biggest losses.
If real accounts are abused, whether through theft or an insider compromise, detection becomes slower and more expensive because the activity appears normal. In 2025, compromised insiders are recognized as the hardest to detect, since their behavior appears legitimate until the infiltrator escalates privileges or moves laterally within the network
- Malice is rare, but the impact is high.
Disgruntled insiders and competitive espionage are less frequent but can lead to IP loss and prolonged recovery.
What an insider incident actually costs
An insider incident costs more than the invoice. It starts with lost business, churn rises, deals slip, and win rates fall. Operations slow next: access freezes, revalidations, rework. Legal and regulatory pressure follows with notifications, audits, and fines, even when the exposure wasn’t malicious. Reputation takes a hit with customers, partners, and talent. And the hardest loss to price is IP damage that lingers well after systems recover.
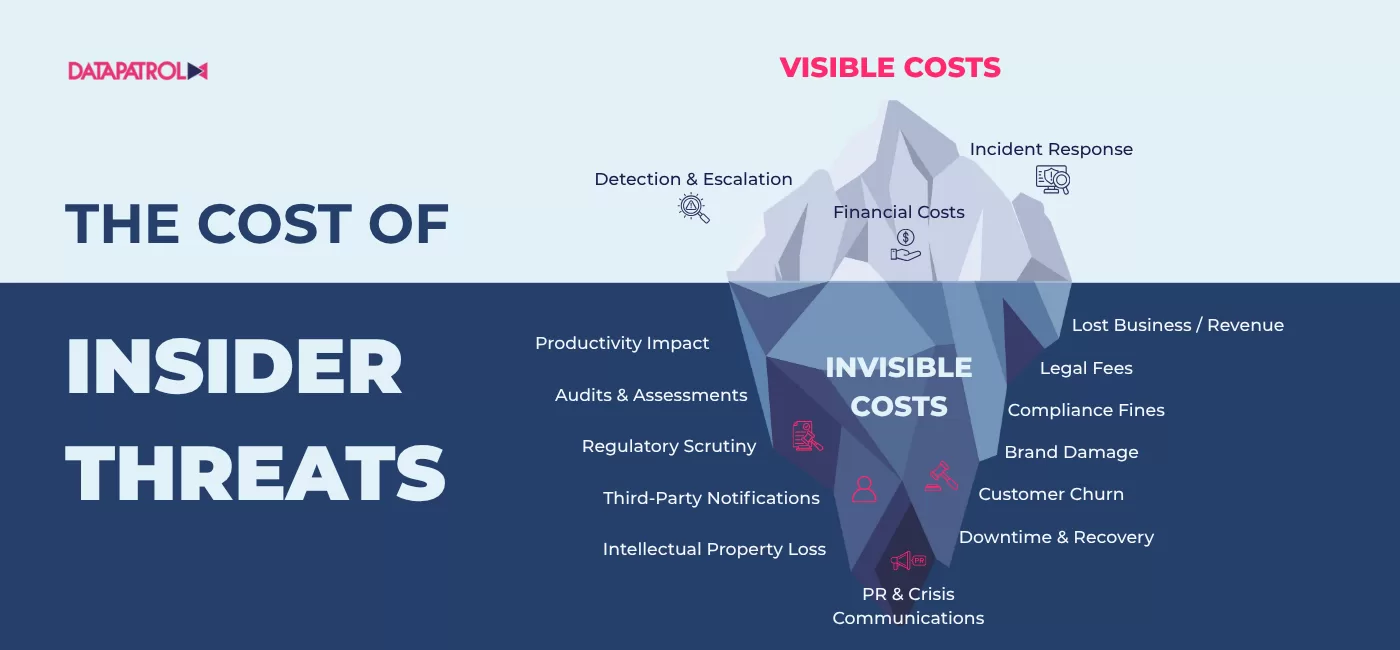
Numbers & Figures: 2025 Insider Risk
- Organizations spent an average of $17.4 million in 2025 to manage insider risk for the year.
- Time multiplies cost: incidents contained within 31 days cost about $10.6 million, while those exceeding 91 days rise to $18.7 million.
- Most teams still spend more reactively than proactively, allocating roughly $211,021 to containment versus $37,756 to prevention.
- The average time to resolve an insider incident is 81 days.
- Forty-one percent of organizations report that their most serious insider event cost between $1 million and $10 million, and nine percent exceeded $10 million.
- Negligent users drive the majority of incidents, accounting for about 55 percent of cases.
- Compromised credentials are the costliest type, averaging approximately $780,000 per incident.
- Malicious insiders represent a smaller share of cases but typically impose high recovery impact.
In summary, the longer it takes to know what happened, who did it, and when it occurred, the higher the bill, and the deeper the consequences.
A simple playbook that works
Define “sensitive when visible.”
Don’t just classify data at rest. Mark the moments and places where it becomes human-readable (key dashboards, exports, portals, shared views).
Attach identity to access and action.
It’s not enough to know who logged in. For sensitive views, keep clear attribution for the session and the on-screen action (view, capture, share).
Narrow privileges by time and task.
Apply just-in-time access for elevated roles. Log changes. Review joiner/mover/leaver events daily.
Cover third parties.
Vendors and contractors should meet the same visibility and attribution standards, write it into contracts, and validate.
Insider risk will always exist where people and data intersect. What matters most is how quickly organizations detect, respond, and learn, turning each incident into an opportunity to strengthen security and trust.
You can also read:
Five Signs Your Organization Needs Screen-Level Data Protection








